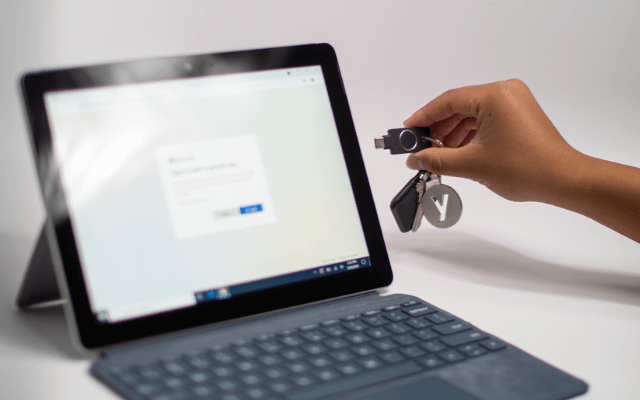
Phishing-resistant MFA for federal agencies
While MFA can be a strong first line of defense against phishing and ransomware, not all forms of MFA are created equal. Legacy authentication methods like usernames and passwords can be easily hacked , and mobile authentication methods like SMS, OTP codes, and push notifications are highly vulnerable to modern phishing attacks, malware, SIM swaps, and man-in-the-middle (MiTM) attacks.
Mobile authentication also creates gaps in your MFA strategy when users cannot, do not want, or will not use mobile authentication due to union restrictions, personal preferences, geographic inconsistencies in the mobile network, financial reasons, and more.
Yubico offers the phishing-resistant, FIPS 140-2 validated YubiKey for multi-factor and passwordless authentication with the highest security. Highly portable and easy to deploy and use, YubiKeys are ideal for users who cannot or do not want to use mobile authentication, helping you achieve 100% MFA coverage and meet your cyber insurance MFA requirements.


Outdated authentication methods are insufficient
Using usernames and passwords or older mobile-based authenticators poses a security risk because usernames and passwords can be easily hacked and SMS, OTP, and push notification apps are highly vulnerable to phishing, account takeover, SIM swapping, and man-in-the-middle (MiTM) attacks.
The advantages of the phishing-resistant YubiKey

Federally compliant phishing-resistant MFA
YubiKeys provide phishing-resistant security and are FIPS 140-2 validated to meet the highest requirements of Authentication Assurance Level 3 (AAL3) of the NIST SP800-63B guidelines, overall Level 1 ( Certificate #3907 ) and Level 2 ( Certificate #3914 ), physical security Level 3. YubiKeys are also CJIS , WebAUTHN, FIDO, FIDO2, and DFARS, as well as NIST SP 800-171 compliant.

Easy deployment and use
YubiKeys integrate seamlessly with existing identity and access management (IAM) and identity provider (IDP) solutions such as Microsoft, Okta, DUO, Ping, and over 1,000 applications and services, including Google Suite, Microsoft Azure, Microsoft Office 365, Box, Jamf, and identity and credential management (ICAM) solutions, eliminating the need to rip and replace existing solutions.

Designed for portability and modern use cases
The YubiKey enables phishing-resistant authentication for privileged users, employees, contractors, mobile users, cloud services, election infrastructure , and even customer-facing digital services. Unlike mobile authentication devices, YubiKeys are phishing-resistant and purpose-built for security, requiring no government-furnished equipment (GFE) or network connectivity. A single YubiKey works across multiple devices, including desktops, laptops, mobile phones, tablets, notebooks, and shared workstations, allowing users to use the same key across all devices. YubiKeys are also highly portable, enabling secure and CJIS-compliant access for users on the move, such as law enforcement and first responders, as well as secure authentication without the use of mobile devices for employees working in correctional departments.

Reduce IT support costs and achieve high ROI
The combination of a seamless user experience, data breach prevention , savings on mobile devices and service costs, and the versatility of the YubiKey with multi-protocol support results in a high ROI for any environment.
The YubiKey not only reduces risk by 99.9%, but is proven to deliver a 203% ROI over 3 years and a 75% reduction in password-related helpdesk tickets.
Demo: YubiKey for mobile BYOAD/BYOD authentication


YubiHSM 2 - the world's smallest HSM for securing communications at the tactical border
Today's armed forces and the network architects who design the communications networks they rely on face increasingly sophisticated adversaries. It is critical that sensitive and classified information is protected in transit and at rest throughout the supply chain.
Public key cryptography plays a key role in securing this data, whether it's CUI data used across the federal government or classified and top secret data secured through the NSA's Commercial Solutions for Classified program. Turnkey solutions for a PKI environment are critical to delivering secure data to the military on the tactical front lines and to remote workers around the globe.
The YubiHSM 2 FIPS is a FIPS 140-2 Level 3 (Certificate No. 3916) validated hardware security module packaged in a portable, low-power nano form factor for secure generation and storage of private key data for rugged computers and tactical devices.